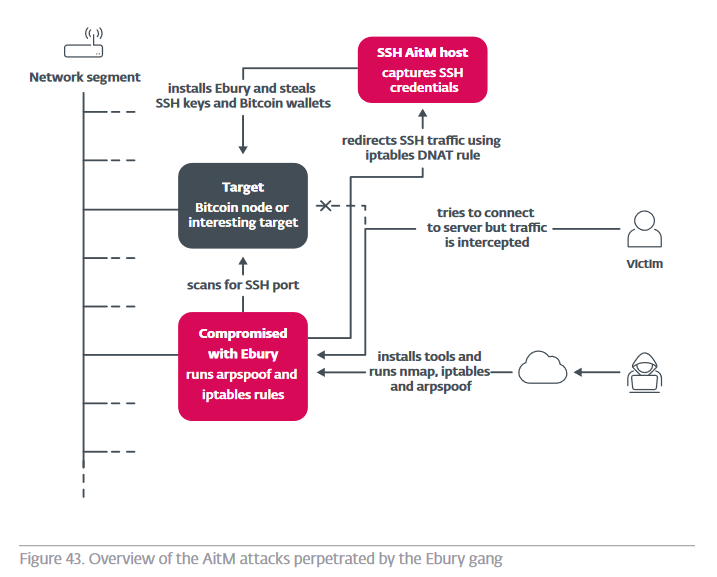
In its new research report, IT security manufacturer ESET has published a report that reveals the malicious activities of the hacker group “Ebury”. Its malware infected more than 400.000 Linux, FreeBSD and OpenBSD servers over the past 15 years.
In the past 18 months alone, 100.000 new victims have been added. In many cases, the Ebury operators were able to gain full access to large servers of Internet providers and well-known hosting providers. The activities of the Ebury group and its botnet over the years have included spreading spam, redirecting web traffic and stealing login credentials. In recent years, the hackers have also moved into credit card and cryptocurrency theft.
Ebury is versatile
Since at least 2009, Ebury has served as an OpenSSH backdoor and credential stealer….
Source link